Security at infoodle is taken seriously.
We have endeavoured to ensure that any data stored with us is kept safe and that the using of the system does not create openings for unauthorized access either by external users, or legitimate users to access data they should not be accessing.
Security is needed to be considered at many points;
Physical security
The servers are hosted by a robust company in Auckland for New Zealand clients, and various Amazon servers for overseas clients. The servers are monitored at various points by infoodle and the hosting company to ensure uptime.
Backups
Two nightly backups are taken and stored in separate physical locations in Auckland together with a 3rd backup held overseas. These are retained for 14 days. Access to the backup files is limited to just infoodle technical people by software configuration.
Traffic security
The data that passes between the user and the server is encrypted using a secure mechanism. You will notice all sites use https rather than http to identify;
Server security
The server is protected using external firewalls and upstream traffic management to control external attacks, and further internal firewalls to provide more advanced protection. Significant steps have been taken to ensure only infoodle technical staff are able to login using special keys and access methods. Should anyone possibly gain access, there are additional internal protocols that are used to control access to the database servers and the databases themselves creating significant problems for anyone trying to gain access unofficially.
infoodle software
The software has been built to ensure that any requests to the server are fully validated in order to prevent unauthorised access to the site.
Permissions
Within infoodle, you have control over what functions people are allowed to have access to, this includes the access to parts of the data e.g. the involvement page (memberships etc) can be hidden. These permissions are given by assigning Roles, Groups permissions and setting Visibility.
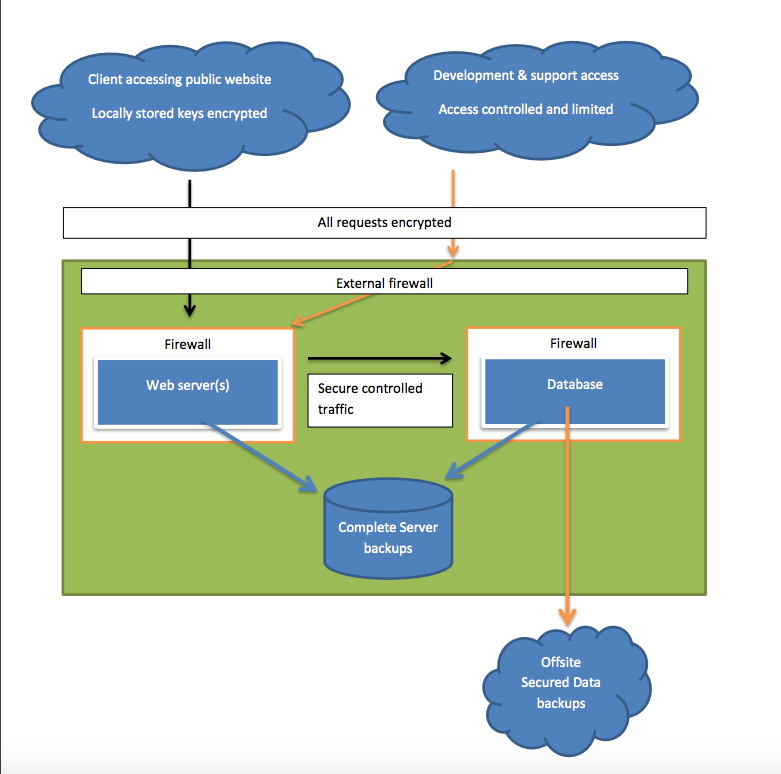
This diagram aims to explain in pictures how the sites are configured at a high level.
Click here for more information on Permissions.